Vulnerabilities continue to grow, hacker groups are rampant, and increasingly complex APT attacks, ransomware, and other cyber attacks are emerging in an endless stream. It is difficult to cope with them relying on conventional protection measures, and we need to think about security issues from the attacker's perspective.
X-Shield automated penetration testing is an effective solution for continuously verify the network security defense system at any time.
Our platform automates offensive security by combining AI with real-world attack methods. It autonomously discovers your assets, uncovers vulnerabilities, verifies their exploitability, and demonstrates the potential impact by simulating lateral movement—all without manual intervention. This provides continuous, actionable security validation that transcends the limitations and high cost of traditional manual testing.
Why can't we anticipate and prevent attacks before they occur?
Traditional security operations tend to focus more on in-process responses and post-incident audits, often lacking investment in proactive prevention and threat anticipation.
Traditional vulnerability scanning emphasizes the quantity and type of vulnerabilities but often lacks an analysis of their exploitability in specific environments and their actual impact on critical business operations.
Our platform automates offensive security by combining AI with real-world attack methods. It autonomously discovers your assets, uncovers vulnerabilities, verifies their exploitability, and demonstrates the potential impact by simulating lateral movement—all without manual intervention. This provides continuous, actionable security validation that transcends the limitations and high cost of traditional manual testing.
Automatically identify attack surface information such as port services.
Automatically detect and verify various system vulnerabilities and WEB application vulnerabilities.
Automatically generate vulnerability exploit payloads, simulate attacks on vulnerabilities, and implement simulated attacks and risk forensics on target systems.
Autonomous decision-making explores all possible attack path chains, automatically executing iterative attacks and lateral movement.
The entire penetration attack process is visualized in the form of an attack chain diagram, clearly showing the penetration process and the location of key risk points.
| Category | Automated penetration testing | Traditional penetration testing | Traditional red teaming | Vulnerability scanning |
|---|---|---|---|---|
| Exploitation | Automatic use of the system | Manual exploitation | Manual exploitation | Not supported |
| Test method | Automation | Manual | Manual | Automation |
| Evaluation frequency | Continuous | Regular | Regular | Regular |
| Test range | Covering all assets | Specific systems and applications | Overall Enterprise | Cover all assets |
| Attack link | Full link | No coverage | Full Link | No coverage |
| Evaluate costs | Low | High | Very high | Middle |
| Speed efficiency | Short time consumption | Long time | Long time | Short time consumption |
| Quantitative indicators | Quantifiable | Limited quantification | Limited quantification | Limited quantification |
| Test results | Low false alarm rate | Depends on the level of the tester | Depends on the level of the tester | High false positive rate |
| Requirements for testers | Low | High | High | Low |
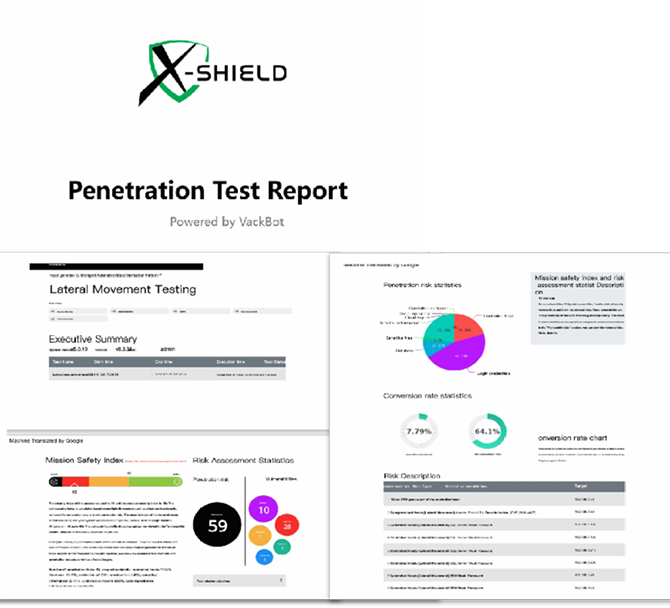
The penetration test report fully records the penetration process and security results, and supports HTML, WORD, PDF and other formats.
What’s in the report?
Contact us now to unlock the full potential of our automated penetration testing services and fortify your security posture!